Pepper Flash Player Download Windows
Tuesday, September 14th, 2021Demo programs have a limited functionality for free, but charge for an advanced set of features or for the removal of advertisements from the program’s interfaces. In some cases, all the functionality is disabled until the license is purchased. Demos are usually not time-limited but the functionality is limited. The DLL-Files Client works on all current Microsoft Windows versions including Windows XP, Vista, 7, 8, 8.1, Windows 10.
- While they don’t seem to be as strict as the ones in the eligibility checker or an ISO, they may still prevent you from installing Windows 11 through Windows Update.
- Here are many possible ways in this post for you to fix DLL errors.
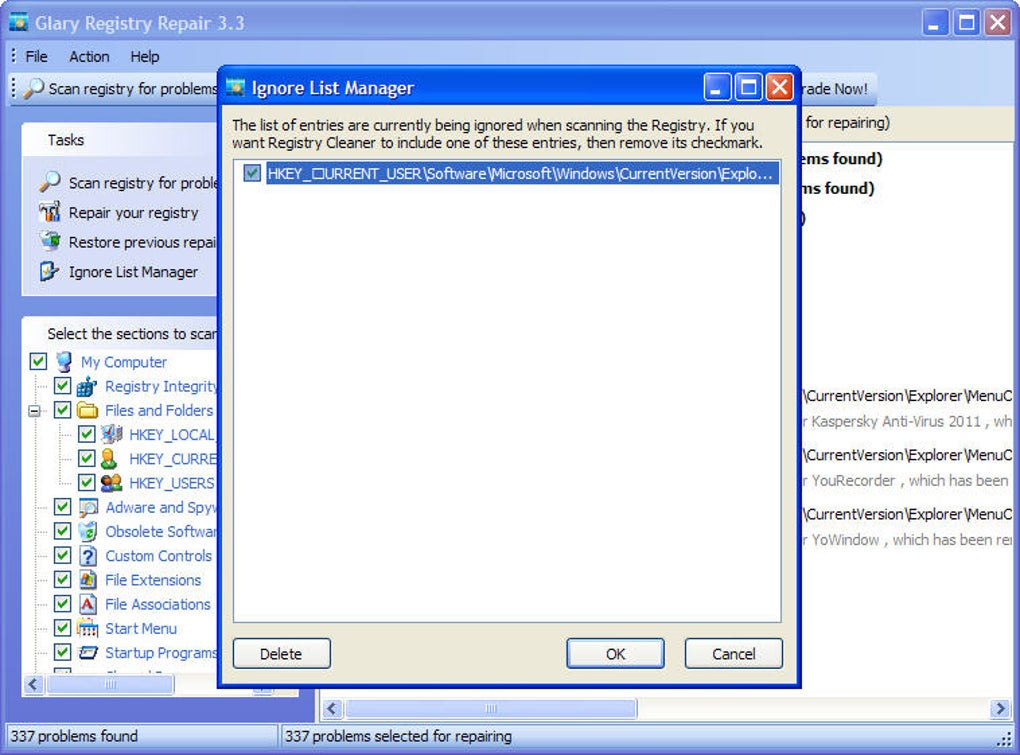
- As soon as you double-click on the .reg file, you will be prompted whether you would like to add or modify the keys using the backup file.
It is not important to only restore the files, but equally, if not more, important to restore the backed up registry too. That is when and why Windows saves the Registry automatically.
Wireshark customization is helpful for security professionals investigating suspicious network traffic. It can be extremely useful when reviewing web traffic to determine an infection chain. Using the methods in this tutorial, we can configure Wireshark’s column display to better fit our investigative workflow. After adding the source and destination port columns, click the “OK” button to apply the changes. These new columns are automatically aligned to the right, so right-click on each column header to align them to the left, so they match the other columns. Malware distribution frequently occurs through web traffic, and we also see this channel used for data exfiltration and command and control activity.
The Facts On Rudimentary Factors Of Dll Errors
You can set your IP address as either automatic or manual (where you hard-code the address). Typically, you’ll want to leave this setting on Automatic .
For example, senders must be careful when calculating RTT samples for retransmitted packets; typically they use Karn’s Algorithm or TCP timestamps . These individual RTT samples are then averaged over time to create a Smoothed Round Trip Time using Jacobson’s algorithm. This SRTT value is what is finally used as the round-trip time estimate.
On Linux systems, you can check that full TCP window scaling is enabled by looking at the value in /proc/sys/net/ipv4/tcp_window_scaling. Windows scaling was introduced in RFC 1323 to solve the problem of TCP windowing on fast, reliable networks. It’s available as an option in any modern TCP implementation. The only question is whether it’s been enabled properly. For example, if you try to write 8192 bytes on each call to write, but one of the calls returns 5691, then you need to send the remaining 2501 bytes on the next call. Otherwise, the client will not see the remainder of this 8K block, and your file will be shorter on the client side than on the server side. Now you have an idea what the TCP window size is about, let’s take a look at a real example of how the window size is used.
Significant Details Of Dll Files – The Facts
TCP uses a sliding window protocol to control the number of bytes in flight it can have. In other words, the number of bytes that were sent but not yet acked. In my simplified test with just a binary that sends TCP data I can see in wireshark that TCP WINDOW ZERO is send by PC .